University of Engg & Tech, Lahore
Dept of Computer Science & Engineering
Final year project
Contact
hiddenbots.army@gmail.com
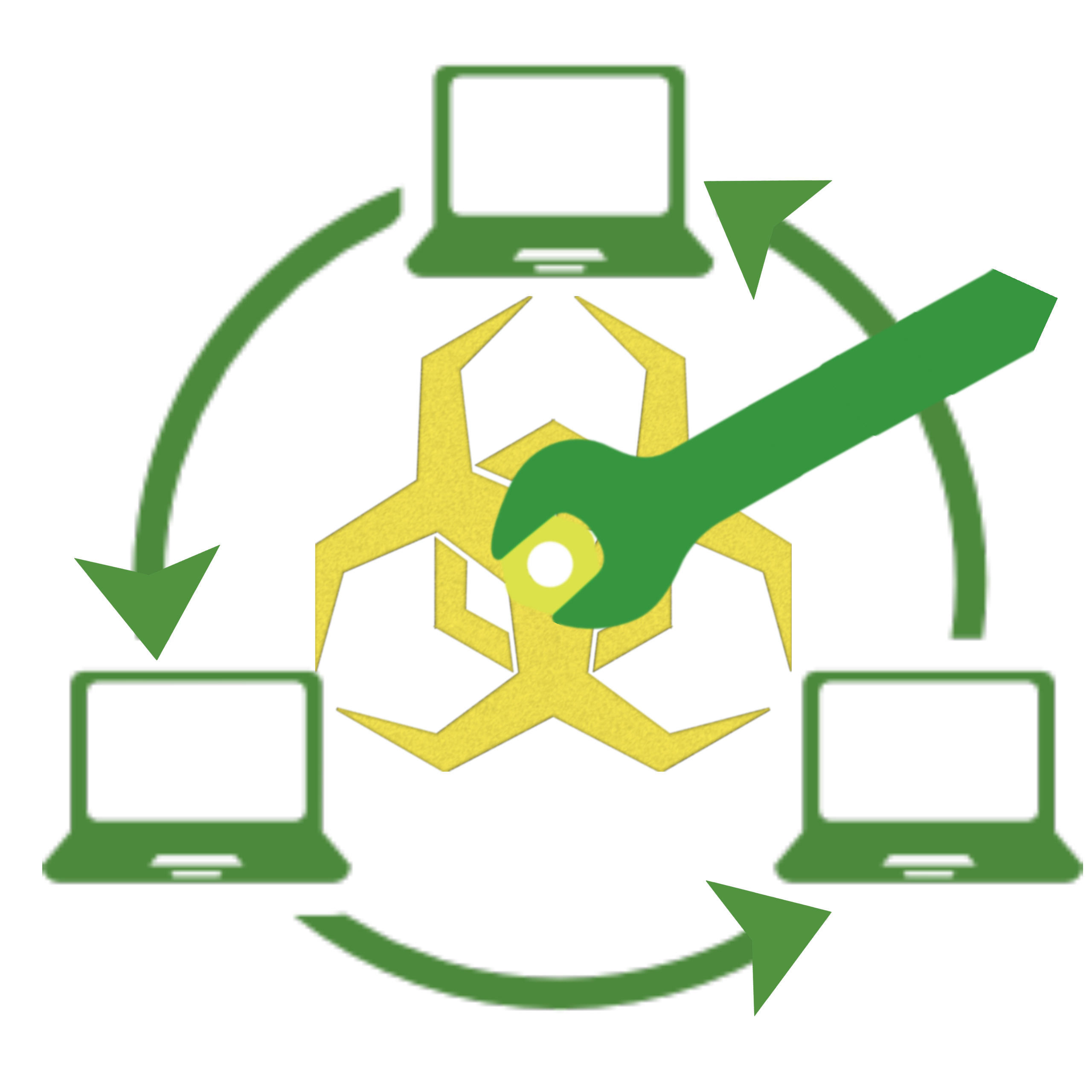
ARMY of HIDDEN BOTs
An autonomous P2P threat detection System
Abstract
Army of Hidden Bots is a p2p threat detection system which operates antivirus in whole p2p network. Each node is able to update antivirus at peer level as if a virus is found in any peer then that peer is able to generate for that specific virus. Signature is then transfered to all other peers in the network so that next time, if that specific virus ia in executable state in any node of network. Our distributed antivirus would be able to detect it & remove it.
Methodology back to top
Tools Created back to top
Signature Tool - back to top
P2P Broadcast - back to top
Lorem the It is a long established fact that a reader will be distracted by the readable content of a page when looking at its layout. The point of using Lorem Ipsum is that it has a more-or-less normal distribution of letters, as opposed to using 'Content here, content here', making it look like readable English. long established fact that a reader will English.
Antivirus - back to top
Lorem the It is a long established fact that a reader will be distracted by the readable content of a page when looking at its layout. The point of using Lorem Ipsum is that it has a more-or-less normal distribution of letters, as opposed to using 'Content here, content here', making it look like readable English. long established fact that a reader will English.
Features back to top
-
BotNet Based Trojan
The Building block of Army is on the basis of Botnet and Trojan horses to monitor the system on which it is residing for security and safety purpose.
-
Capability Enhancement
Our System is an Intelligent Enough to Autonomously Manages the new updates which needs no guidance for its operations.
-
Intruder Identification
If malicious process is detected in computer, it will recognize it as an antivirus to user record the information about that process and also have the capability to remove it.
-
No Point of failure
Our system finds its uniqueness as there is no dependency of peers because in master-slave architecture if master dies everything fails.
Copyright © hiddenbots.github.io